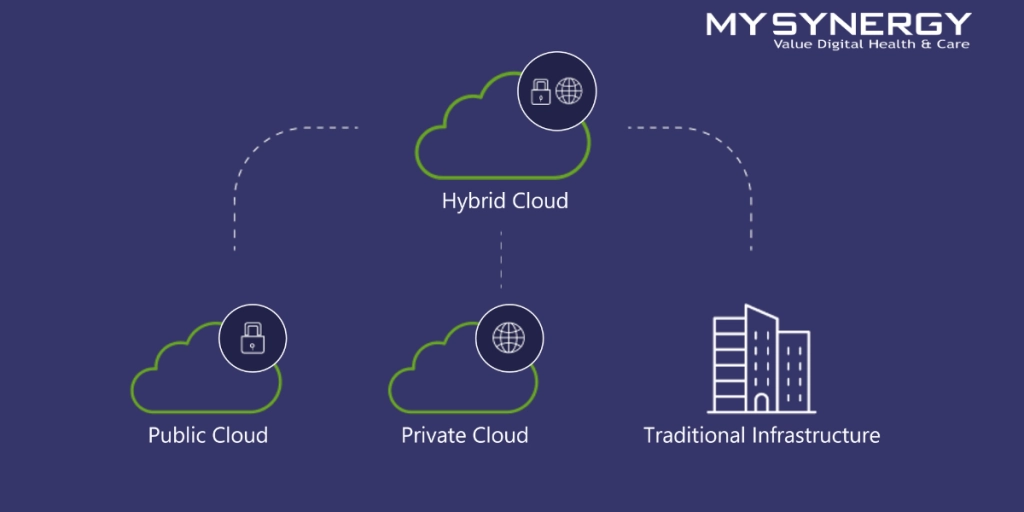
Enhancing Cloud Security with a Mixed Cloud Approach
As organizations increasingly adopt hybrid or multi-cloud environments, ensuring robust security measures becomes paramount. Mixed cloud security encompasses a range of considerations and practices that address the unique challenges presented by combining public cloud services, private cloud infrastructure, and on-premises resources. This blog post will explore the key features and benefits of a mixed cloud security approach, highlighting the importance of unified visibility, modern monitoring, user and access security, vulnerability scanning, next-generation security operations, and backup and disaster recovery solutions.
Unified Visibility
One of the fundamental aspects of mixed cloud security is having a unified view of the security posture across different cloud platforms. Whether you utilize Azure, AWS, Google Cloud, or a combination of these services, a unified visibility solution enables you to monitor and manage security effectively. This holistic approach enhances your ability to identify potential risks, detect attacks, and respond promptly to threats.
Modern Monitoring
A comprehensive security information and event management (SIEM) solution is essential to proactively identify and respond to sophisticated threats. Modern monitoring tools empower organizations to collect data at scale, encompassing users, devices, applications, and infrastructure across multiple clouds and on-premises environments. These tools minimize false positives and provide actionable insights for rapid threat detection, investigation, and response, leveraging advanced analytics and threat intelligence.
Users & Access Security
Securing access to the connected world for all users, smart devices, and services is critical to mixed cloud security. By implementing robust identity and access management practices, organizations can protect every app and resource, ensuring access is granted only to authorized individuals. With simplified sign-in experiences, intelligent security measures, and unified administration, organizations can enhance productivity while maintaining a strong security posture.
Vulnerability Scanning and Assessments
Detecting and mitigating risks across managed and unmanaged endpoints is essential for a comprehensive security strategy. Vulnerability scanning and assessments help organizations identify potential weaknesses and proactively address them. By continuously monitoring assets and leveraging contextual recommendations, security teams can prioritize vulnerabilities based on business impact and remediate them efficiently. With coverage across various platforms and devices, including Linux, macOS, Windows, and network devices, organizations can ensure comprehensive vulnerability management.
Next-Generation Security Operations
The landscape of cybersecurity threats constantly evolves, requiring organizations to adopt next-generation security operations. Security operations centers (SOCs) can efficiently triage incidents and respond effectively by utilizing intelligent security analytics, automation rules, and built-in playbooks. These advanced tools empower organizations to detect, investigate, and respond to emerging threats while benefiting from Microsoft's comprehensive threat intelligence and AI capabilities. Cloud-native solutions further reduce the total cost of ownership, allowing organizations to focus on strengthening their security posture.
Backup and Disaster Recovery
Data protection and disaster recovery are critical to any organization's security strategy. A mixed cloud security approach includes end-to-end backup and disaster recovery solutions that are simple, secure, scalable, and cost-effective. By seamlessly integrating with on-premises data protection solutions, organizations can ensure timely recovery during service disruptions, accidental deletions, or data corruption. Built-in security controls protect data from ransomware and accidental deletions, reducing the complexity and costs of maintaining on-premises disaster recovery infrastructure.
Embracing a mixed cloud security approach is crucial for organizations seeking to safeguard their data, applications, and infrastructure across hybrid and multi-cloud environments. By leveraging unified visibility, modern monitoring, user and access security, vulnerability scanning, next-generation security operations, and robust backup and disaster recovery solutions, organizations can fortify their security posture and protect against emerging threats. With the right tools and practices in place, organizations can confidently embrace the benefits of the cloud while maintaining a strong and resilient security foundation.
Unified Visibility
One of the fundamental aspects of mixed cloud security is having a unified view of the security posture across different cloud platforms. Whether you utilize Azure, AWS, Google Cloud, or a combination of these services, a unified visibility solution enables you to monitor and manage security effectively. This holistic approach enhances your ability to identify potential risks, detect attacks, and respond promptly to threats.
Modern Monitoring
A comprehensive security information and event management (SIEM) solution is essential to proactively identify and respond to sophisticated threats. Modern monitoring tools empower organizations to collect data at scale, encompassing users, devices, applications, and infrastructure across multiple clouds and on-premises environments. These tools minimize false positives and provide actionable insights for rapid threat detection, investigation, and response, leveraging advanced analytics and threat intelligence.
Users & Access Security
Securing access to the connected world for all users, smart devices, and services is critical to mixed cloud security. By implementing robust identity and access management practices, organizations can protect every app and resource, ensuring access is granted only to authorized individuals. With simplified sign-in experiences, intelligent security measures, and unified administration, organizations can enhance productivity while maintaining a strong security posture.
Vulnerability Scanning and Assessments
Detecting and mitigating risks across managed and unmanaged endpoints is essential for a comprehensive security strategy. Vulnerability scanning and assessments help organizations identify potential weaknesses and proactively address them. By continuously monitoring assets and leveraging contextual recommendations, security teams can prioritize vulnerabilities based on business impact and remediate them efficiently. With coverage across various platforms and devices, including Linux, macOS, Windows, and network devices, organizations can ensure comprehensive vulnerability management.
Next-Generation Security Operations
The landscape of cybersecurity threats constantly evolves, requiring organizations to adopt next-generation security operations. Security operations centers (SOCs) can efficiently triage incidents and respond effectively by utilizing intelligent security analytics, automation rules, and built-in playbooks. These advanced tools empower organizations to detect, investigate, and respond to emerging threats while benefiting from Microsoft's comprehensive threat intelligence and AI capabilities. Cloud-native solutions further reduce the total cost of ownership, allowing organizations to focus on strengthening their security posture.
Backup and Disaster Recovery
Data protection and disaster recovery are critical to any organization's security strategy. A mixed cloud security approach includes end-to-end backup and disaster recovery solutions that are simple, secure, scalable, and cost-effective. By seamlessly integrating with on-premises data protection solutions, organizations can ensure timely recovery during service disruptions, accidental deletions, or data corruption. Built-in security controls protect data from ransomware and accidental deletions, reducing the complexity and costs of maintaining on-premises disaster recovery infrastructure.
Embracing a mixed cloud security approach is crucial for organizations seeking to safeguard their data, applications, and infrastructure across hybrid and multi-cloud environments. By leveraging unified visibility, modern monitoring, user and access security, vulnerability scanning, next-generation security operations, and robust backup and disaster recovery solutions, organizations can fortify their security posture and protect against emerging threats. With the right tools and practices in place, organizations can confidently embrace the benefits of the cloud while maintaining a strong and resilient security foundation.